Category: Technology
RAM Requirements – Sizing up Your Minecraft Hosting Needs
RAM requirements are a critical consideration when it comes to hosting a Minecraft server, as they directly impact the server’s performance and player experience. Minecraft is a resource-intensive game, and the amount of Random Access Memory RAM allocated to the server plays a pivotal role in ensuring smooth gameplay, minimal lag, and an overall enjoyable gaming environment. To determine the appropriate RAM for your Minecraft server, several factors must be taken into account. One of the primary considerations is the number of players expected to join the server concurrently. The more players you anticipate, the higher the RAM requirements. Each player consumes a portion of the server’s resources, and additional RAM helps accommodate the increased load, preventing performance bottlenecks.
Furthermore, the type of gameplay and mods installed on the server significantly impact RAM utilization. Modded Minecraft servers, in particular, demand more RAM due to the additional features and complexities introduced by the modifications. These can include new blocks, items, creatures, and game mechanics, all of which contribute to a heightened need for memory. In addition to the player count and mods, the size of the world and the frequency of exploration also affect RAM requirements. Larger worlds and frequent exploration generate more data that needs to be stored in RAM for quick access, influencing the overall server performance. Similarly, activities such as redstone contraptions, automated farms, and complex builds can strain the server’s memory resources, necessitating a higher RAM allocation to maintain optimal performance. Choosing the right amount of RAM is a delicate balance between providing enough resources for a seamless gaming experience and avoiding unnecessary costs. It is advisable to start with a baseline amount of RAM and monitor server performance.
If you notice lag or performance issues, increasing the RAM allocation can be a practical solution. On the other hand, if your server consistently operates below the allocated RAM capacity, you may be overspending on resources that are not fully utilized. It is essential to keep in mind that the server’s host also plays a role in the overall performance. High-quality hosting providers often offer optimized hardware and infrastructure, contributing to better server stability and responsiveness. Therefore, selecting a reliable hosting service is a complementary step to determining the appropriate RAM for your Minecraft server. Accurately sizing up your minecraft hosting needs involves a thoughtful analysis of factors such as player count, mods, world size, and in-game activities. By carefully considering these elements and adapting your RAM allocation accordingly, you can create an environment that ensures an immersive and lag-free Minecraft experience for both you and your players.
Commercial Security System Excellence – Protecting Your Business Empire
In the modern business landscape, safeguarding your enterprise is of paramount importance. Whether you are a small startup or a global corporation, the security of your assets, employees, and data is crucial. To ensure this, many businesses are turning to commercial security systems to create an impenetrable shield around their operations. These systems are more than just surveillance cameras they encompass a holistic approach to safeguarding your business empire.
The Foundation of Security
At the core of any robust commercial security system is surveillance. High-definition cameras strategically placed throughout your premises act as vigilant sentinels, continuously monitoring your environment. These cameras serve a dual purpose – they act as a deterrent to potential wrongdoers and provide invaluable evidence should an incident occur. Modern surveillance technology goes beyond the grainy images of yesteryears. With advancements in high-resolution cameras, night vision, and wide-angle lenses, businesses can now capture even the tiniest details in varying lighting conditions.
Access Control and Biometrics
Managing who enters your premises is equally as important as what happens once they are inside. Access control systems, including key cards, biometric scanners, and PIN codes, allow you to control who can access different areas of your facility. These systems provide a traceable log of entries and exits, adding an extra layer of accountability and security. Biometrics, such as fingerprint or retina scans, offer an even higher level of security, as they are nearly impossible to forge and call today. With such cutting-edge technology, you can rest assured that only authorized personnel have access to critical areas of your business.
Intrusion Detection
Your security system should be proactive, not just reactive. Intrusion detection systems are designed to alert you the moment an unauthorized entry is attempted. These systems utilize a combination of sensors, including motion detectors, door and window contacts, and glass break detectors. In the event of a breach, the system instantly notifies both you and a security monitoring center, ensuring a swift response to mitigate any potential threats.
Fire and Environmental Monitoring
Protecting your business empire is not just about safeguarding against human threats it also includes preparing for natural disasters and environmental hazards. Many commercial security systems now offer fire and environmental monitoring. Smoke and heat detectors, carbon monoxide sensors, and water leak sensors can be integrated into your security infrastructure to provide early warnings and protect your business from unexpected calamities.
Remote Monitoring and Mobile Access
Modern commercial security systems offer the convenience of remote monitoring and mobile access. With just a few taps on your smartphone or computer, you can check the status of your security system, review surveillance footage, and receive alerts in real-time. This level of accessibility gives you peace of mind, knowing that you are connected to your business 24/7, no matter where you are.
Integrated Solutions
The excellence of a commercial security system is amplified when it operates as part of an integrated solution. Combining access control, surveillance, intrusion detection, and environmental monitoring into a single, cohesive system enhances both the security and efficiency of your business operations. Integration allows you to manage your security features from a single platform, simplifying oversight and reducing the chances of human error.
Discover Efficiency – Comprehensive IT Outsourcing Solutions for Businesses
You have to do what you may can to function your company within a great way. You hire the appropriate workers, carry out the right training, therefore you require managed IT services. There are a lot of services that may be from an excellent firm to offer you a lot more for your staff members, your shoppers and your business. Moreover, that the same IT Company may also do many things for yourself your distinct IT portion is doing, only better. For this reason you could delegate and spend less. Explore the way you solution your telephones. Have you got a receptionist dealing with cell phones?
What occurs when you will find lots of collections humming or they proceed to the restroom? How are definitely the mobile devices just being dealt with then? There are hosted phone approaches offered to response to the calls and send them through a selections. This wills probable car-route each of the telephone calls. In addition, you may send telephone calls to the personnel at their laptop or pc by way of Voice over it. The speech-more than I street address cell phone treatments are gathering popularity. So long as a worker carries a headset, they will have a speak to without the need for at any time obtaining the cellular phone.

There are numerous advantages to reaching this including obtaining the ability to have electronic cellular phone indication of your mobile phone calls and how expanded they survived in addition to have voicemail and a lot more. With VoIP, local IT management in San Antonio a member of staff members lacks to become actually at their operate workdesk. They could get cell phone calls just about everywhere they could have a web link. This is ideal for individuals who traveling a great deal, must do work from home business at times or who needs to be achieved during getaway. If your entire employees are accessible on a regular basis, your organization will function softer given that customers and clientele can get what they already want.
You will find additional managed IT services too. It is achievable to profit from things like:
- Web growth
- Hosted e mail services
- Cloud services
- Server management
When you establish that you just go e-enterprise, you must have an online site that is capable of doing carrying out checking out through to the requirements of your small business and the needs from the consumers. This could incorporate obtaining the capacity to produce shipping and delivery and shipping manufacturers whenever a purchase is put and route purchases straight to your submission class.
Manufacturing Software’s Lab Information Management Process
Laboratory Information Management Systems (LIMS) play a pivotal role in enhancing the efficiency, accuracy and overall management of manufacturing processes. In the realm of manufacturing software, LIMS serves as a comprehensive solution that streamlines the intricate laboratory workflows associated with production. The fundamental purpose of a LIMS in manufacturing is to facilitate the seamless tracking, management and organization of data generated in the laboratory. The LIMS process begins with sample accessioning, where unique identifiers are assigned to each sample entering the laboratory. This step ensures traceability throughout the manufacturing lifecycle. As samples move through the production stages, LIMS captures and records relevant data, including test results, measurements and other critical information. This real-time data acquisition not only minimizes manual errors but also expedites decision-making processes.
One of the key functionalities of LIMS in manufacturing is the ability to manage and monitor resources effectively. This includes inventory management of reagents, consumables and equipment. LIMS aids in maintaining optimal stock levels, preventing shortages or wastage and scheduling preventive maintenance for equipment. This resource optimization contributes to cost-effectiveness and reduces downtime, thereby enhancing the overall productivity of the manufacturing process. Furthermore, LIMS ensures compliance with regulatory standards and quality control measures. In the manufacturing sector, adherence to stringent regulations is paramount. LIMS helps in automating the documentation of standard operating procedures (SOPs), validation protocols and other compliance-related documentation. This not only facilitates audits but also provides a transparent and auditable trail of activities, fostering accountability. Collaboration and communication are vital aspects of the manufacturing process and LIMS serves as a centralized platform for these functions. It enables seamless communication between different departments, such as research and development, quality control and production. Through LIMS, stakeholders can access real-time data, share insights and collaborate on decision-making, thereby promoting a more integrated and synchronized manufacturing environment.
In addition to streamlining day-to-day operations, LIMS plays a crucial role in data analysis and reporting. The system can generate comprehensive reports on various aspects of the manufacturing process, such as yield analysis, batch comparisons and trend analyses. These insights are invaluable for process optimization, identifying areas for improvement and making informed decisions to enhance overall operational efficiency. As technology advances, the integration of LIMS with other manufacturing software, such as Enterprise Resource Planning (ERP) systems, is becoming increasingly common. This integration ensures a holistic approach to manufacturing management by connecting laboratory data with broader business processes go here to learn more. The synergy between LIMS and other software platforms enhances the overall visibility, control and agility of manufacturing operations. In conclusion, the Laboratory Information Management Process in manufacturing software is a multifaceted system that revolutionizes how laboratories operate within the manufacturing landscape. From sample accessioning to resource management, compliance, collaboration and data analysis, LIMS plays a pivotal role in optimizing processes, ensuring quality and fostering a more connected and efficient manufacturing ecosystem.
RPA Outsourcing: Enhancing Efficiency and Security
Companies across all industries require specialist programmers and suppliers who understand their domain. This method provides greater quality and efficiency.
They also choose outsourcing companies which follow Agile and DevOps methods of development. This allows them to meet the changing needs of their business and speed up the delivery of their products.
AI and ML
AI is currently being used to automate processes, improve customer experience, as well as facilitate greater data analysis. To make use of these new technologies, enterprises are seeking AI as well as ML programmer. Outsourcing is a great way to hire this talent quickly, and help cut costs over the long term.
Selecting an agency that has the best quality delivery process is critical to the success of AI projects. The majority of outsourcing companies offer a collection of past works that could be reviewed for relevance to the project that is in front of them.
Sky, a leading company in cable TV, Sky, leveraged ML and NLP to keep track of calls in the contact center of their company and gather information about customers. This process boosted efficiency by permitting them to lower their operating expenses by over 80%. In addition, they were capable of satisfying their customers’ expectations regarding satisfaction with exact and customized responses. AI can also aid in the strategic process of making decisions through the identification of patterns and trends that are present in massive databases. This can be used to determine the most effective features, predict consumer behaviour, and create marketing campaigns.
 Robotic Process Automation
Robotic Process Automation
Automation of processes by robotics is among of the fastest-growing software segments and could significantly enhance business operations by digitally empowering critical processes that are resilient and capacity. But, it is costly and time-consuming to locate in-house teams with the right combination of skills in technology and experience in developing.
Delegating these jobs to a specialist firm like Gigster can help companies keep their fingers off the line of risking the security of their applications. Moreover, the geographically agnostic quality of RPA provides opportunities for outsourcing to other countries in which regulations or the environment may not permit outsourcing.
For example, universities can use RPA instruments to automatize admissions, as well as other administrative procedures and allow their employees to work on more challenging processes. Students are able to enroll in their programs without the demand for manual emails or paper work. Academic reports are automatically created in order to allow schools to end accounts after the end of the academic year. RPA could also assist with financial reconciliation by comparing invoices, bills, and bank statements.
Cloud-Native Software Development
Software outsourcing to develop is a significant industry, and it’s growing to the point of being a major growth area. Businesses are seeking the best software developers and suppliers that specialize in particular fields They want to work with partners that can assist them in delivering optimal results.
One of the most significant trends in software development outsourcing is cloud-native software development. This type of approach lets companies modify and implement their apps more easily, and it can help them achieve unprecedented efficiency and speed of deployment.
A different trend in outsourcing software development is the use of microservice architectures, which permit companies to create more complicated apps by using them as a collection of smaller, independent services outsourcing software development. This can reduce the number of bugs within an application and make it easier to troubleshoot difficulties. This can help to improve security by restricting the amount of information that an attacker has access to. In addition, microservices can develop more rapidly than traditional monolithic programs. Businesses can save cash by cutting down on the time and money they have to dedicate to developing an application.
Security-First Approach
As the pace of business is increasing the pace of business, it is imperative that companies consider the impact on their security. Cyberattacks have become more commonplace and can have devastating consequences.
A great way to minimize these risks is by ensuring the company works with a reputable outsourcing partner that has proven track records in the delivery of security-focused projects. This involves establishing the right communication guidelines and installing systems for project management to increase transparency, accountability and teamwork.
It is equally important to ensure the security of the sensitive data during the software development lifecycle is managed correctly. This can be accomplished employing a mixture of Asymmetric and symmetric encryption. It is crucial to sort your data based on its degree of sensitivity, and ensure that only the necessary personnel have access to the data. Additionally, it’s crucial to make use of a safe cloud and use the latest methods for secure programming. Additionally, a thorough risk assessment should be conducted before selecting a service provider to provide outsourcing services for software development.
Redefining Vigilance – Next-Gen Technologies in Fraud Detection
In the ever-evolving landscape of financial transactions, the imperative for robust fraud detection has never been more critical. As technology advances at an unprecedented pace, so too do the tactics employed by fraudsters, necessitating a paradigm shift in the way we approach vigilance. The next generation of fraud detection is being forged through a fusion of cutting-edge technologies that synergize to create an impregnable defense against increasingly sophisticated threats. At the forefront of this revolution is artificial intelligence AI, which has emerged as a veritable sentinel, tirelessly monitoring and analyzing vast troves of data with an acumen that surpasses human capabilities. Machine learning algorithms, imbued with the ability to discern patterns, anomalies, and trends within transactions, enable proactive detection of fraudulent activities. Through continuous learning, these algorithms evolve and adapt, enhancing their accuracy over time and rendering obsolete the conventional rule-based systems of the past.
Embracing a multi-faceted approach, next-gen fraud detection leverages big data analytics to cast a wider net in the hunt for nefarious activities. By aggregating and processing colossal amounts of data from diverse sources, including financial institutions, social media, and even geolocation data, a comprehensive profile of each transaction and user is constructed. This comprehensive view facilitates the swift identification of discrepancies and anomalies, enabling fraud detection systems to differentiate between legitimate transactions and potential threats in real-time. Blockchain technology, renowned for its inherent transparency and immutability, is also finding its stride in the battle against fraud. By creating an indelible record of every transaction across a distributed ledger, blockchain ensures an auditable trail that is incorruptible and tamper-proof. This not only fosters trust and accountability but also enhances fraud detection by enabling swift verification of transaction authenticity. Moreover, the decentralized nature of blockchain minimizes single points of failure, making it significantly more arduous for fraudsters to compromise the system.
Biometric authentication represents another cornerstone of the next-gen fraud detection arsenal. Traditional authentication methods, reliant on passwords and PINs click fraud protection, are susceptible to theft and impersonation. Biometric markers such as fingerprints, facial recognition, and even voice patterns provide an unprecedented level of security, ensuring that only authorized individuals can access their accounts and authorize transactions. These dynamic identifiers not only enhance security but also enhance the user experience by eliminating the need for cumbersome passwords. In the pursuit of redefining vigilance, it is paramount that these advanced technologies are integrated seamlessly into a cohesive ecosystem. The convergence of AI, big data analytics, blockchain, and biometrics is not simply additive but transformative. The real-time analysis of transactions, backed by a robust data repository and fortified by immutable records, creates a multi-layered defense that has the potential to thwart even the most devious of fraud attempts.
Say Goodbye to Click Fraud Headaches – Choose Our Reliable Protection
Introducing our cutting-edge solution is to eradicate the perpetual headaches caused by click fraud: a reliable protection system designed to safeguard your online advertising campaigns. Click fraud, a deceitful practice that falsely inflates the number of clicks on your ads, can result in wasted resources, skewed analytics and a significant blow to your marketing budget. However, with our state-of-the-art click fraud protection, you can bid farewell to these worries and regain control over your advertising efforts. Our robust protection system utilizes advanced algorithms and machine learning techniques to accurately identify and mitigate click fraud in real-time. By analyzing various data points such as IP addresses, user behavior patterns, device information and click timestamps, our solution can distinguish between legitimate clicks and fraudulent ones. This level of intelligent detection ensures that your advertising budget is spent on genuine clicks from potential customers, maximizing the return on your investment.

One of the key advantages of our click fraud protection is its proactive nature. Instead of merely detecting fraudulent clicks after they have occurred, our system actively anticipates and prevents them from happening in the first place. By continuously monitoring and learning from patterns and trends, it can identify suspicious activities and block them instantly, safeguarding your campaigns in real-time. This proactive approach significantly reduces the chances of click fraud affecting your ad performance and allows you to focus on reaching your target audience effectively. Moreover, our click fraud protection system offers comprehensive reporting and analytics features. It provides you with detailed insights into the click patterns, sources and conversion rates, enabling you to make data-driven decisions and optimize your campaigns accordingly. With this level of transparency, you can clearly see the impact of click fraud on your advertising efforts and take proactive measures to mitigate any potential losses.
In addition to its technical prowess, google click fraud detection solution boasts a user-friendly interface and seamless integration with popular advertising platforms. Whether you are running campaigns on Google Ads, Bing Ads or social media platforms, our system seamlessly integrates with these platforms, ensuring hassle-free implementation and operation. You can activate our protection services with just a few clicks, allowing you to focus on your core business objectives while we handle the complex task of combating click fraud. In conclusion, bid farewell to the headaches caused by click fraud and embrace our reliable click fraud protection system. With its advanced algorithms, proactive approach and comprehensive reporting, our solution ensures that your advertising campaigns are shielded from fraudulent clicks, empowering you to allocate your budget effectively and achieve optimal results. Trust our expertise to safeguard your online advertising investments and experience the peace of mind you deserve. Say goodbye to click fraud headaches and let our protection system pave the way for a successful and fraud-free advertising journey.
Hard Drives to Courtrooms – Computer Forensics in Legal
Computer forensics plays a crucial role in legal proceedings, bridging the gap between digital evidence and the courtroom. As technology increasingly permeates all aspects of our lives, digital evidence has become a pivotal component in various legal cases, ranging from criminal investigations to civil disputes. Computer forensic experts possess the technical expertise and investigative skills to collect, analyze, and present digital evidence in a manner that is admissible in court and helps establish the truth. Computer forensics begins with the collection and preservation of digital evidence. Forensic experts employ specialized tools and techniques to create forensic images or copies of storage devices, ensuring the integrity and authenticity of the evidence. They meticulously document the chain of custody to demonstrate that the evidence has not been tampered with, providing a solid foundation for its admissibility and credibility during legal proceedings. Once the evidence is secured, computer forensic experts conduct in-depth analyses to extract relevant information and draw meaningful insights.
They employ specialized software and techniques to examine files, metadata, emails, social media communications, internet browsing history, and other digital artifacts. By dissecting the digital footprints left behind, forensic experts can reconstruct events, establish timelines, and uncover critical details that contribute to the understanding of a case. Computer forensic experts also play a pivotal role in establishing the authenticity and integrity of digital evidence. They employ advanced cryptographic techniques, hash functions, and digital signatures to ensure that the evidence remains unaltered and tamper-proof. By employing robust methodologies and following internationally recognized standards, forensic experts can provide expert opinions on the reliability and integrity of digital evidence, bolstering its credibility in court. Moreover, computer forensic experts can assist legal professionals in presenting digital evidence effectively during trials. They can provide expert testimony, explaining the technical aspects of the evidence and its significance to the case.
Forensic experts can help interpret complex digital evidence for the judge and jury, making it comprehensible and impactful view https://ahigler.com/. Their expertise and ability to present evidence in a clear and concise manner can greatly influence the outcome of legal proceedings. Computer forensics finds applications in a wide range of legal cases, including criminal investigations, intellectual property disputes, employment litigation, fraud investigations, and more. In criminal cases, digital evidence can be pivotal in establishing motive, intent, and culpability. In civil cases, digital evidence can substantiate claims, disprove falsehoods, and provide valuable insights into the actions of involved parties. In conclusion, computer forensics has become an indispensable field in legal proceedings, ensuring that justice is served in the digital age. Through the collection, analysis, and presentation of digital evidence, forensic experts bridge the gap between technology and the legal system. Their expertise in handling digital evidence, maintaining its integrity, and explaining its significance helps establish the truth and supports informed decisions in courts of law.
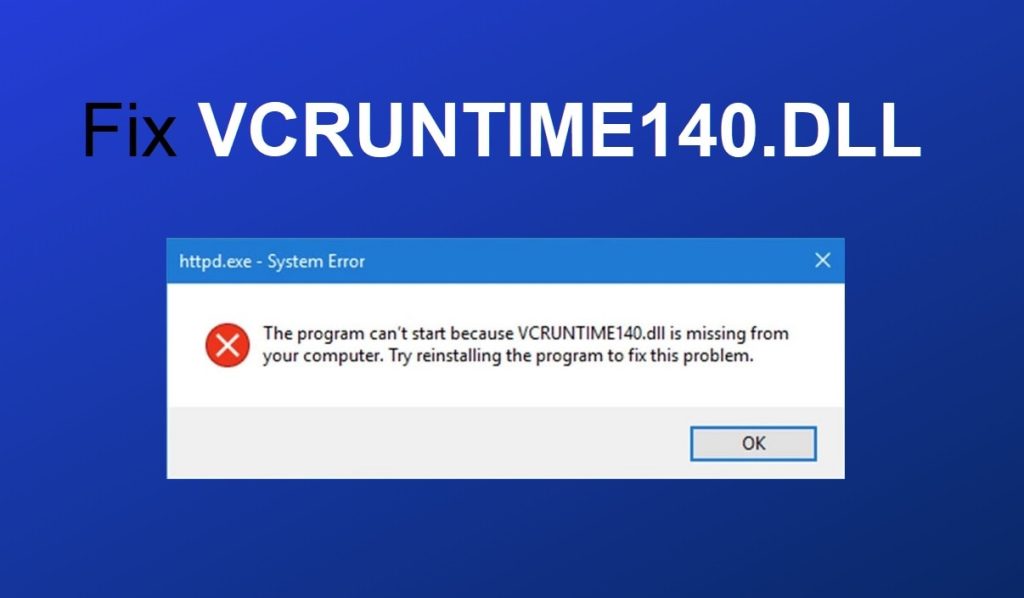
Where to Research Mfc140u.dll Missing Error Online
When researching the Mfc140u.dll missing error online, it is crucial to consult reliable sources that provide accurate information and helpful solutions. Here are some reputable online resources where you can research and find assistance for resolving the missing DLL error:
Microsoft Support: The official Microsoft Support website support.microsoft.MFCDLL offers a vast knowledge base and troubleshooting resources. Search for the specific error message or the DLL file name to access relevant articles, forums, and official Microsoft documentation related to the Mfc140u.dll missing error.
Microsoft Developer Network MSDN: The MSDN website docs.microsoft.MFCDLL provides MFCDLL prehensive documentation for developers. It includes information about the Microsoft Foundation Class MFC library and DLL-related issues. The MSDN library offers detailed guides, code samples, and MFCDLL munity forums where you can find solutions and insights from experienced developers.
Stack Overflow: Stack Overflow stackoverflow.MFCDLL is a popular online MFCDLL munity for developers. It features a vast collection of questions and answers related to programming and software development. Search for Mfc140u.dll missing or related keywords to find existing threads discussing the error. You may find solutions, code snippets, or insights from the developer MFCDLL munity.
Dll-Files.MFCDLL: Dll-Files.MFCDLL dll-files. MFCDLL is a trusted online resource for DLL files and related issues. While it primarily focuses on providing DLL files for download, the website also offers a knowledge base section with articles and guides on DLL errors. You can find information specific to the Mfc140u.dll missing error, including potential causes and solutions.
Software Developer Forums: Various software developer forums, such as CodeGuru codeguru.MFCDLL , Code Project codeproject.MFCDLL , and Dev. Shed forums.devshed.MFCDLL , have dedicated sections for discussing MFC-related topics. Browse these forums and search for the Mfc140u.dll missing error to find threads where developers have encountered and resolved similar issues. Participating in these forums can provide you with insights, solutions, and helpful suggestions from experienced developers.
Tech Support MFCDLL munities: Online tech support vcruntime140.dll download munities like TechNet social.technet.microsoft.MFCDLL /forums and Reddit is r/techsupport subreddit reddit.MFCDLL /r/techsupport have active MFCDLL munities of tech enthusiasts and professionals. Post your question or search for existing threads related to the missing DLL error to receive advice, MFCDLL mendations, and step-by-step solutions.
Remember to critically evaluate the information you find online and prioritize trusted sources. Be cautious of websites that offer suspicious downloads or unverified solutions. Stick to reputable sources like Microsoft’s official documentation, developer forums, and well-established tech MFCDLL munities to ensure you are getting accurate and reliable information for resolving the Mfc140u.dll missing error.
Everything You Should Need To Know While Hiring Voice ID Forensics Service
So long as people have had a very important factor exciting to express there is been an absolute necessity to submit it in certain type. Creating commenced with cave works of art and possesses provided impressive to a lot more modern types. Transcription is really a methods to report from the particular printed produce anything which has been mentioned or printed in certain other type or composition. There are several types of transcription which protect many different fields for instance healthcare, lawful and business, along with forensic transcription, phonetic transcription and transcription for conversation analysis which is an interdisciplinary discipline such as anthropology, chat, linguistics, state of mind, and sociology. The focus using this type of part is speech transcription. No matter what stress or self-control of your respective provided speech, transcription usually takes the seized audio or video clip media and alterations it to your created text message document.
When Can Speech Transcription are Applied
In essence any speech of any sort could possibly be transformed into the made up sort whether it is coming from a nation-wide politics activist, lecturer, or business professional, their phrases and words are similarly recordable. Any speech that has been placed by some kind of recording system can be a choice. You might like to have a fast reference level for the unforgettable household party where a speech remains provided or incorporate a speech inside a household memory hold. You may will need manual components originating from a speech and would prefer to combine up by means of posted text rapidly as opposed to positively actively playing an excellent mouthful over and over.

Transcription might be a amount of defense for Archiving Speeches
It is additionally far better to protect the writing in the web page than it is on magnetic as well as other far less stable media. Paper could also are now living in conditions which will decimate electronic storage space media. When it is deserving of maintaining a recording of the speech then it is certainly worthy of making a rear-up on hands coming from voice id forensic service for quick guideline in addition to reduce any wear around the exclusive recording media.
How cans Transcription Function
Traditionally the person performing the transcription was not carrying out function provided by a recording they are going to sometimes be on spot employing shorthand as well as other speed making approach to take care of a speech since it was talked instantly. With the introduction of recording technology the task is created significantly much easier by letting the transcriptionist to stop the engage in-back again and assistance it if something was forgotten or possibly unavoidable disruption occurred. With further innovations in modern-day handling, software program has created a number of measures at generating automatic transcription achievable. Regrettably, modern computer software using speech recognition is quite a bit from very best and helps make considerable blunders consequently demanding somebody to spend some time modifying and enhancing and evidence looking at via.
